Functions | |
| None | dump_merkle_tree (List[bytes] mk_tree) |
| MixResult | parse_mix_call (Any mixer_instance, Any tx_receipt) |
| MixResult | wait_for_tx_update_mk_tree (MixerClient zeth_client, MerkleTree mk_tree, str tx_hash) |
| Tuple[ZethNote, ZethNote, ExtendedProof, List[int], JoinsplitSigKeyPair] | get_mix_parameters_components (MixerClient zeth_client, ProverClient prover_client, MerkleTree mk_tree, OwnershipKeyPair sender_ownership_keypair, List[Tuple[int, ZethNote]] inputs, List[Tuple[ZethAddressPub, EtherValue]] outputs, EtherValue v_in, EtherValue v_out, Optional[ComputeHSigCB] compute_h_sig_cb=None) |
| MixResult | bob_deposit (MixerClient zeth_client, ProverClient prover_client, MerkleTree mk_tree, str bob_eth_address, mock.KeyStore keystore, Optional[EtherValue] tx_value=None) |
| MixResult | bob_to_charlie (MixerClient zeth_client, ProverClient prover_client, MerkleTree mk_tree, Tuple[int, ZethNote] input1, str bob_eth_address, mock.KeyStore keystore) |
| MixResult | charlie_withdraw (MixerClient zeth_client, ProverClient prover_client, MerkleTree mk_tree, Tuple[int, ZethNote] input1, str charlie_eth_address, mock.KeyStore keystore) |
| MixResult | charlie_double_withdraw (MixerClient zeth_client, ProverClient prover_client, IZKSnarkProvider zksnark, MerkleTree mk_tree, Tuple[int, ZethNote] input1, str charlie_eth_address, mock.KeyStore keystore) |
| MixResult | charlie_corrupt_bob_deposit (MixerClient zeth_client, ProverClient prover_client, IZKSnarkProvider zksnark, MerkleTree mk_tree, str bob_eth_address, str charlie_eth_address, mock.KeyStore keystore) |
Variables | |
| string | ZERO_UNITS_HEX = "0000000000000000" |
| int | BOB_DEPOSIT_ETH = 200 |
| int | BOB_SPLIT_1_ETH = 100 |
| int | BOB_SPLIT_2_ETH = 100 |
| int | BOB_TO_CHARLIE_ETH = 50 |
| int | BOB_TO_CHARLIE_CHANGE_ETH = BOB_SPLIT_1_ETH - BOB_TO_CHARLIE_ETH |
| float | CHARLIE_WITHDRAW_ETH = 10.5 |
| float | CHARLIE_WITHDRAW_CHANGE_ETH = 39.5 |
Function Documentation
◆ bob_deposit()
| MixResult test_commands.scenario.bob_deposit | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| MerkleTree | mk_tree, | ||
| str | bob_eth_address, | ||
| mock.KeyStore | keystore, | ||
| Optional[EtherValue] | tx_value = None |
||
| ) |
◆ bob_to_charlie()
| MixResult test_commands.scenario.bob_to_charlie | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| MerkleTree | mk_tree, | ||
| Tuple[int, ZethNote] | input1, | ||
| str | bob_eth_address, | ||
| mock.KeyStore | keystore | ||
| ) |
◆ charlie_corrupt_bob_deposit()
| MixResult test_commands.scenario.charlie_corrupt_bob_deposit | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| IZKSnarkProvider | zksnark, | ||
| MerkleTree | mk_tree, | ||
| str | bob_eth_address, | ||
| str | charlie_eth_address, | ||
| mock.KeyStore | keystore | ||
| ) |
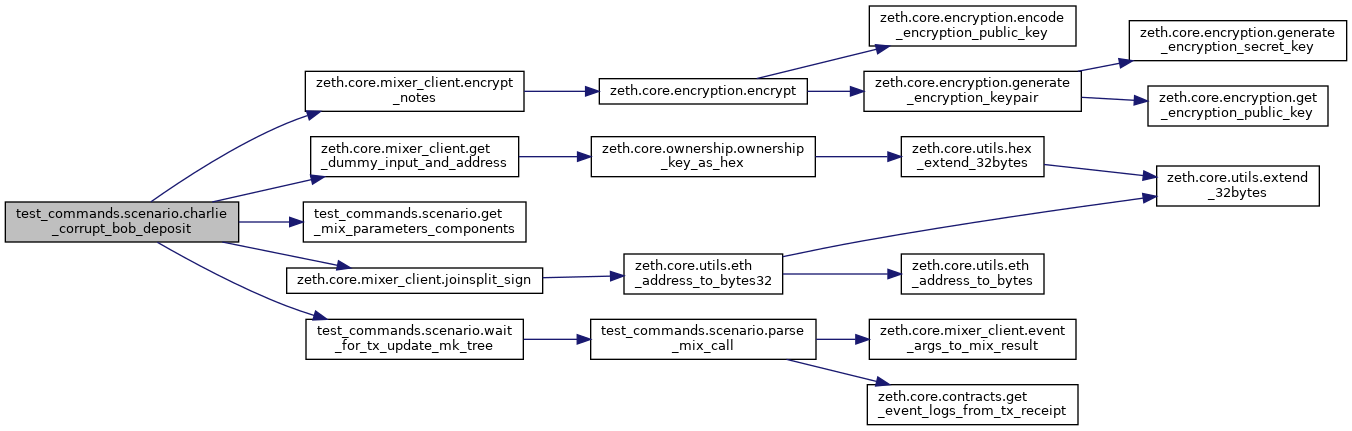
Charlie tries to break transaction malleability and corrupt the coins bob is sending in a transaction She does so by intercepting bob's transaction and either: - case 1: replacing the ciphertexts (or sender_eph_pk) by garbage/arbitrary data - case 2: replacing the ciphertexts by garbage/arbitrary data and using a new OT-signature - case 3: Charlie replays the mix call of Bob, to try to receive the vout Both attacks should fail, - case 1: the signature check should fail, else Charlie broke UF-CMA of the OT signature - case 2: the h_sig/vk verification should fail, as h_sig is not a function of vk any longer - case 3: the signature check should fail, because `msg.sender` will no match the value used in the mix parameters (Bob's Ethereum Address). NB. If the adversary were to corrupt the ciphertexts (or the encryption key), replace the OT-signature by a new one and modify the h_sig accordingly so that the check on the signature verification (key h_sig/vk) passes, the proof would not verify, which is why we do not test this case.
Definition at line 336 of file scenario.py.
Here is the call graph for this function:
◆ charlie_double_withdraw()
| MixResult test_commands.scenario.charlie_double_withdraw | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| IZKSnarkProvider | zksnark, | ||
| MerkleTree | mk_tree, | ||
| Tuple[int, ZethNote] | input1, | ||
| str | charlie_eth_address, | ||
| mock.KeyStore | keystore | ||
| ) |
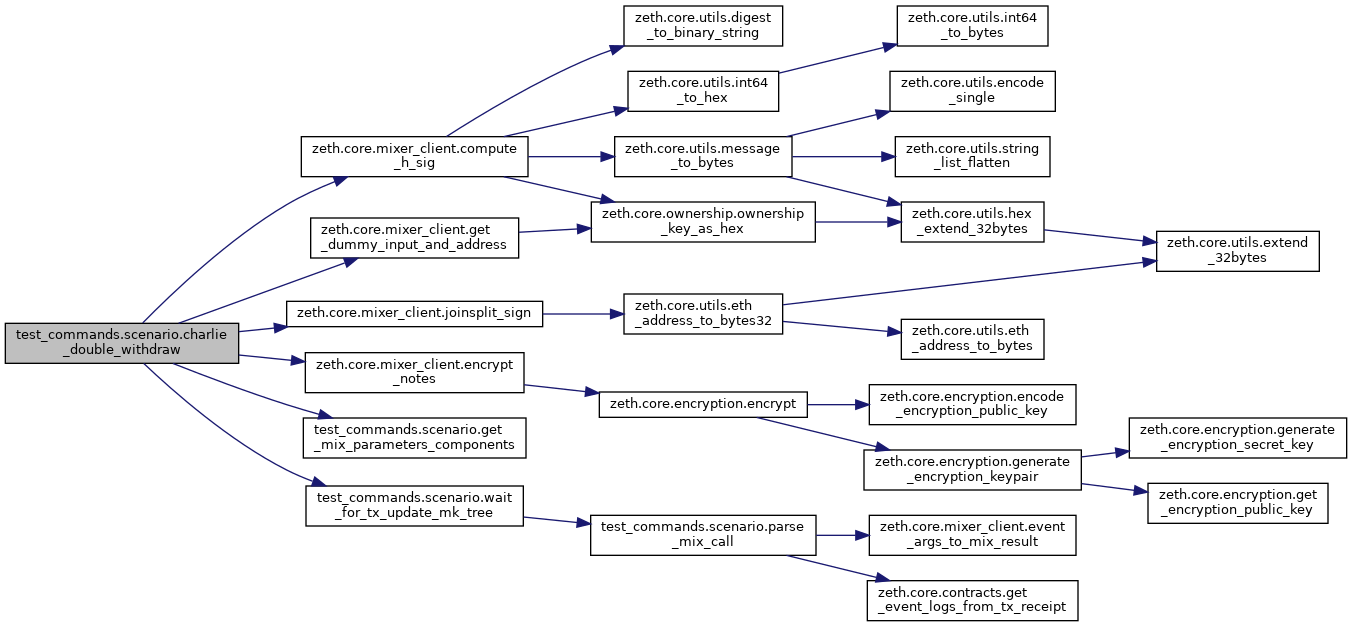
Charlie tries to carry out a double spending by modifying the value of the nullifier of the previous payment
Definition at line 200 of file scenario.py.
Here is the call graph for this function:
◆ charlie_withdraw()
| MixResult test_commands.scenario.charlie_withdraw | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| MerkleTree | mk_tree, | ||
| Tuple[int, ZethNote] | input1, | ||
| str | charlie_eth_address, | ||
| mock.KeyStore | keystore | ||
| ) |
◆ dump_merkle_tree()
| None test_commands.scenario.dump_merkle_tree | ( | List[bytes] | mk_tree | ) |
Definition at line 37 of file scenario.py.
◆ get_mix_parameters_components()
| Tuple[ZethNote, ZethNote, ExtendedProof, List[int], JoinsplitSigKeyPair] test_commands.scenario.get_mix_parameters_components | ( | MixerClient | zeth_client, |
| ProverClient | prover_client, | ||
| MerkleTree | mk_tree, | ||
| OwnershipKeyPair | sender_ownership_keypair, | ||
| List[Tuple[int, ZethNote]] | inputs, | ||
| List[Tuple[ZethAddressPub, EtherValue]] | outputs, | ||
| EtherValue | v_in, | ||
| EtherValue | v_out, | ||
| Optional[ComputeHSigCB] | compute_h_sig_cb = None |
||
| ) |
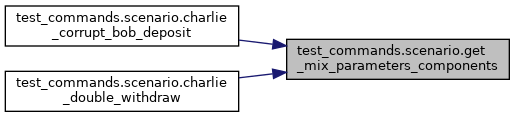
Manually create the components required for MixParameters. The tests below manipulate these to create custom MixParameters as part of attacks.
Definition at line 69 of file scenario.py.
Here is the caller graph for this function:
◆ parse_mix_call()
| MixResult test_commands.scenario.parse_mix_call | ( | Any | mixer_instance, |
| Any | tx_receipt | ||
| ) |
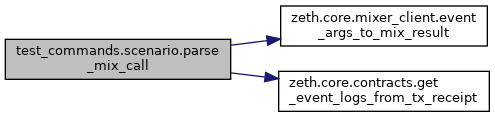
Get the logs data associated with this mixing
Definition at line 43 of file scenario.py.
Here is the call graph for this function:
Here is the caller graph for this function:
◆ wait_for_tx_update_mk_tree()
| MixResult test_commands.scenario.wait_for_tx_update_mk_tree | ( | MixerClient | zeth_client, |
| MerkleTree | mk_tree, | ||
| str | tx_hash | ||
| ) |
Definition at line 55 of file scenario.py.
Here is the call graph for this function:
Here is the caller graph for this function:
Variable Documentation
◆ BOB_DEPOSIT_ETH
| int test_commands.scenario.BOB_DEPOSIT_ETH = 200 |
Definition at line 26 of file scenario.py.
◆ BOB_SPLIT_1_ETH
| int test_commands.scenario.BOB_SPLIT_1_ETH = 100 |
Definition at line 27 of file scenario.py.
◆ BOB_SPLIT_2_ETH
| int test_commands.scenario.BOB_SPLIT_2_ETH = 100 |
Definition at line 28 of file scenario.py.
◆ BOB_TO_CHARLIE_CHANGE_ETH
| int test_commands.scenario.BOB_TO_CHARLIE_CHANGE_ETH = BOB_SPLIT_1_ETH - BOB_TO_CHARLIE_ETH |
Definition at line 31 of file scenario.py.
◆ BOB_TO_CHARLIE_ETH
| int test_commands.scenario.BOB_TO_CHARLIE_ETH = 50 |
Definition at line 30 of file scenario.py.
◆ CHARLIE_WITHDRAW_CHANGE_ETH
| float test_commands.scenario.CHARLIE_WITHDRAW_CHANGE_ETH = 39.5 |
Definition at line 34 of file scenario.py.
◆ CHARLIE_WITHDRAW_ETH
| float test_commands.scenario.CHARLIE_WITHDRAW_ETH = 10.5 |
Definition at line 33 of file scenario.py.
◆ ZERO_UNITS_HEX
| string test_commands.scenario.ZERO_UNITS_HEX = "0000000000000000" |
Definition at line 25 of file scenario.py.
 1.8.17
1.8.17